Risk management - Identify the risks and responses
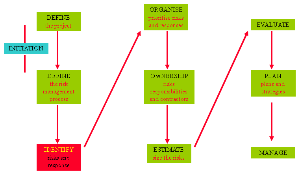
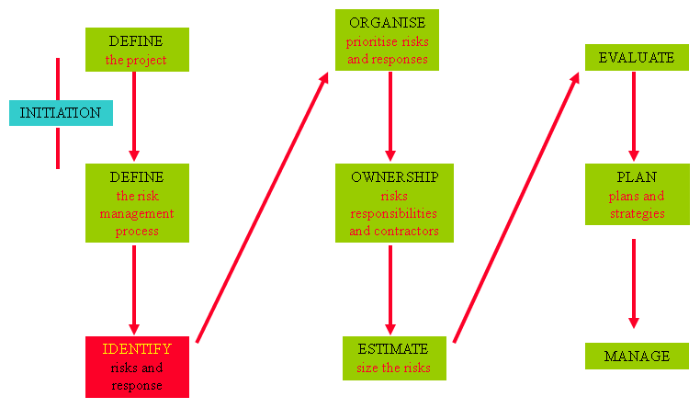
The Risk Management process
IDENTIFY (the risks and responses)
It is all too easy to identify a risk and the first thought is ‘what is its impact on the project?’
It is important to understand the impact of any risk because in knowing this the project manager will be able to prioritise any resource in order to minimise the potential affect.
However, if the underlying cause is not clearly identified the ‘response’ to try to reduce the occurrence of the risk may be poorly targeted.
As we have mentioned previously [see What are the core process steps to assess a risk?], the responses can be ‘proactive’ or ‘reactive’. The former will generate actions to be incorporated in the activity base plan (schedule) and the latter will exist as contingency plans, should the risk materialise.
This early identification of both the risks and their responses is the key to a good risk management process.
Do not just concentrate on the identification and impact on the project, delaying the responses until later.
The nature of this process will ensure we don’t:
- Waste time identifying responses that are unnecessary
- Overlook any responses
- Miss a small issue which has no apparent solution
In order to find the risks we can employ suitable problem solving techniques:
- Brain storm
- Interview
- Checklists etc.
Having completed the list we will then need to order them in some fashion so that suitable resource can be allocated.
For every risk there MUST be a response, even if this is ‘do nothing and accept the risk’.
It is a good idea to just start the exercise with a pencil and a blank sheet of paper.
When a risk has been identified it should be unambiguous in its definition.
It is not uncommon for this process of in depth consideration of responses to lead to the identification of ‘opportunities’ within the project.
Assessing the risks and responses
At this stage it is a good idea to have some understanding of a ‘rank’ of the risks.
The terms ‘primary’ and ‘secondary’ risks are usually reserved for the ‘main’ risks derived from the plan (the former) while the latter are those risks existing as a result of the ‘responses’.
WHO:
Within any project there will be a number of stakeholders. If significant risk is identified requiring extra expenditure the stakeholder’s approval may need to be sought.
For example, as a project progresses there may need to be a new appraisal of safety factors driven by regulatory bodies. This may require changes to product design or other significant aspects of the project. These modifications may prove very expensive.
One key problem for longer term projects is to try an predict the future in terms of regulatory constraints.
Another major source of risk are contractors and subcontractors. This applies to any areas where control is reduced.
Any third party should be carefully selected, monitored and suitably motivated.
This will be covered in more detail elsewhere [see The contractor].
When selecting a third part several problems can arise:
- They may not indicate their true experience in the project, which is difficult to verify
- Poor estimate of the work involved and the cost
- It may be difficult to ascertain if the third party is putting in the required amount of effort
- The split of risk allocation between the parties may prove difficult
- There may be a difference of opinion when assessing risk from the client versus third party perspective as each will have different motivations and will have a tendency to manage risk to their own ends
- Even if the third party is within the same organisation there may still be problems
Most of these problem areas should be managed by contracts. Even with these in place problems can exist.
- Poor definition of terms
- Payment and claims arrangements
- Liabilities for problems with anything produced
Any project delays may allow third parties to escape penalties in areas that were not directly affected by the problem.
WHAT:
If a project has technological hurdles it may be tempting to avoid these using simpler methods and a different strategy.
Whilst this tactic may reduce risk it could open the door to competitors who are willing to take on the higher risk of more advanced technologies.
In an ideal world once the product design is completed it will never change. This is very unlikely to be the case and even more so for long running projects.
Design may have to be updated during the project which will bring attention to any change control procedures.
These should allow for good assessment, coordination and documentation of changes.
The selection of appropriate resource may not be available if particular skills are required.
It is best to try to manage the quantity of resource at a constant level rather than have it going up and down on a regular basis.
There may be a need to employ local labour.
WHEN:
The duration of a project can vary enormously. It is not unusual for there to be pressures to complete within a particular time frame.
The overall duration is often challenged. This is a healthy situation as it will make you consider and justify the schedule.
The main starting point is the Gantt chart or schedule based upon a work breakdown structure.
The Project Life Cycle (PLC)
The Project Life Cycle contains:
- Concept
- Plan
- Execute
- Termination
It is probably best to carry out a risk assessment process during the plan phase. Whatever phase is chosen the aim is to identify risks that don’t unexpectedly materialise during the latter phases of the PLC.
Each stage of the PLC has its own issues to be address:
ConceptAt this early stage there is a lack of definition of the product and appropriate objectives.
PlanRegulatory bodies need consideration as do the activity plans. It is easy to miss risks here.
Cost and resource estimates may not be accurate.
Allocation of responsibilities and dealing with contracts and terms and conditions.
Selection of third parties.
Implementing monitoring and control and progress reporting procedures.
Developing good communication procedures and channels together with effective leadership.
A need to act on any realised risks, implement contingency plans at triggers and respond to missed milestone objectives.
Review newly identified risks and future implications.
Many problems occur due to either human error or management error. Human error is exacerbated by complex projects, new technology, the pressure of work activities and general uncertainty.
TerminationInstigate proper field testing and training procedures as necessary.
Reviewing the project to retain the experience gained and examine any lessons learnt.
Identification of any liabilities.
More in depth search for risks
It is often a good idea to explore a potential risk in more depth.
Once a risk is identified we can investigate it further by asking additional questions.
For example: If there is a risk of adverse weather.
- What is the chance of it happening?
- What might be the affect of the adverse weather? The problem may not just be chance of project delay but possible safety problems or even a knock on effect on another part of the project.
Taking it to another level we may ask:
- How reliable is the data?
- What liabilities might occur etc?
Categorising responses
Having ascertained a particular risk we will need to identify and record a response even if this is ‘do nothing’.
Bear in mind that the first determined response may not be the best or the most risk efficient. It is good practice to consider several responses and if necessary apply more than one in parallel.
We may consider the following options:
Change the objectives.This may include a modification of the plan before sorting out contracts in a proactive manner. It may require relaxation of performance criteria as a reactive response.
Allowing adequate time [see 'The Complete Time Management package'] to prepare plans is vital to make them realistic. Any changes will need to be assessed for cost implications and the knock on effect in other areas of the project. We may wish to prioritise certain criteria to third parties by saying ‘cost is more important then time’ or vice versa.
It might seem easy to just pass on the risk to a third party via suitable contractual terms. This will only work if they manage risk in an efficient manner.
Even so there will still be a limited amount of risk that will need appropriate management from you.
In this case we are trying to promote those events which will nullify the possibility of the risk materialising. This is where the identification of any opportunities may be useful.
Risk alleviationHere we will be trying to reduce the impact of the risk or modifying some aspect of the source of the risk in order to try to reduce its likelihood.
Contingency plans.As mentioned elsewhere [see Types of plans], these are plans put into place on the chance that a risk will happen. In practice, it is more likely that a ‘trigger’ will exist to implement the plan when it looks as though the risk is about to occur. The trigger will minimise any time delays due to the risk arising. This will mean you reserving resource or finance for its implementation.
Delay the decision.This gives you a bit of breathing space. We may wish to do this to gather new data or better evaluate existing data to formulate an improved strategy for future use.
Delay the risk assessment.This step in effect delays a risk assessment on the grounds that we will ‘keep an eye on the situation’. We should be aware of the costs and issues involved as well as formulating benefits. You may feel that the situation will become ‘clearer’ later but it could also get worse.
Risk recognition.Here you just recognise that the risk may happen but you will not proactively do anything. There will be a belief that that if and when the risk materialises management will be able to handle it adequately.
Naturally, there will be many risks within a project that should be handled well, as they arise, with the expertise on hand. Just maintaining a ‘flexible approach’ to risk management often ends in tears.
It is good for morale to identify ‘primary’ risk responses as soon as possible.
Secondary risks and responses
Secondary risks occur where the ‘response’ to the primary risk, in its self, causes a problem. Consideration of these may influence the original design that caused the primary risk.
Major problems often occur when primary responses fail to work.
Obtaining the list of risks
The only way to achieve a list of risks and responses is to ask people.
This means all those involved in the project not just the project manager and his immediate team.
You will need to invite the comment of a wide variety of personnel e.g. finance, legal, engineering, sales, lawyers etc.
To gain suitable comment will be difficult at a single meeting unless the project is small.
A variety of techniques exist to collect opinion:
- Brain storm
- Interview
- Checklists etc.
Naturally, to get opinion from all concerned may need a combination of these approaches with all the data being discussed at separate meetings until it is felt all risks and appropriate responses have been identified.
There may be an element of not raising particular risks if these were apparently managed well in the past.
Past experiences may not be applicable to future projects.
The most common technique is the brain storm but check lists can be quick and useful.
However, they suffer from:
- Interdependence of schedule activities are hard to visualise
- Over years the list to consider can get quite long and risks identified are not readily prioritised
- If its not on the list it is likely to be ignored
- The list may be orientated to a particular project
- Necessary detail may be lacking
- Can promote a simple view of risks and the risk management process
Any checklist used should be considered as an initial help to a more formal procedure.
Brain storm and individual interview are probably the best options to use.
Ideally, the identification of risks should be as complete as possible before going on to the next phase.
Other risks will materialise but you want to make sure all major risks are identified at this stage.